Cyber security compliance in 2026 isn’t optional—it’s survival. Discover how ignoring regulations like NIS2, DORA, and evolving NIST rules could lead to massive fines, breaches, and business collapse. Stay ahead now. In 2026, cyber security compliance has evolved from a checklist item into a make-or-break business imperative. With AI-powered attacks accelerating, geopolitical tensions fueling cyber
Why CSAM is a Critical Term Every Security Pro Should Know in 2026
CSAM in cybersecurity means Cybersecurity Asset Management: the key to visibility, risk reduction, and defense in 2026. Why every security professional must master it now. (148 caractères) In 2026, blind spots in your digital environment are no longer acceptable. With AI-driven attacks accelerating and attack surfaces exploding, CSAM in cybersecurity—Cybersecurity Asset Management—has become non-negotiable. This
Using Online Casino-Style Strategy to Outsmart Hackers & Protect Your Data
Cybersecurity advice often sounds technical, abstract, and detached from how people actually make decisions under pressure. That is part of the problem. Attackers rarely win because they have magical tools. They win because most people make rushed choices, trust the wrong signal, or leave too much exposed at once. That is why the logic behind
Why Zero-Trust Security Is No Longer Optional For Federal Agencies
Federal agencies no longer operate inside predictable network boundaries. Cloud adoption, remote work, and complex vendor ecosystems have reshaped how government systems connect and exchange data. However, many security models still rely on assumptions that no longer hold up. Zero-trust shifts the focus from location-based trust to continuous verification. Instead of asking whether someone sits
Top 10 Cyber Security Companies Every Web Developer Should Know
Discover the top cyber security companies that matter for web developers — from Cloudflare and Snyk to Auth0 and Burp Suite. Free tiers, use cases, and how to build your security stack You don’t need an enterprise security team. You need the right tools built for developers who ship code and manage web infrastructure. Most
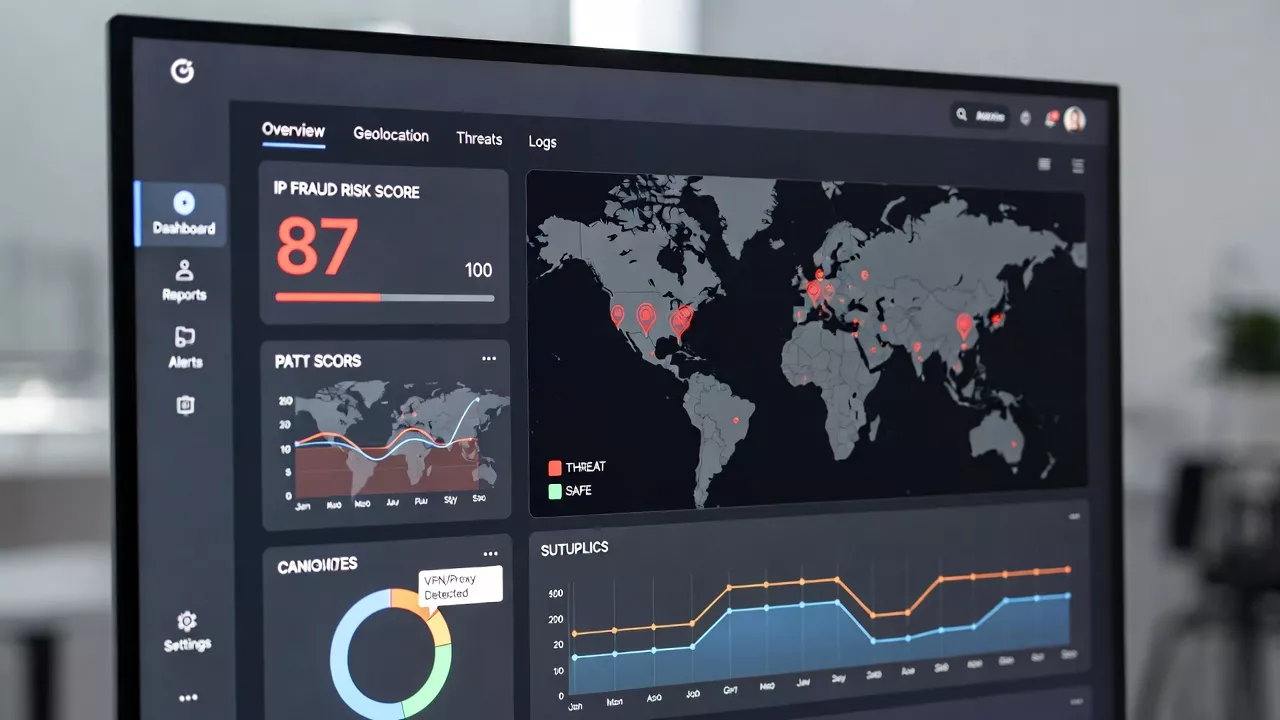
Scamalytics: How IP Fraud Scoring Works and Why Your Website Needs It
How this IP fraud detection tool works, why it matters for web developers, and how to integrate it into your PHP projects to block scammers in real time. If you run a website — whether it’s an e-commerce store, a membership platform, or a network of content sites — you’re a target for fraud. Bots,
How Colleges Can Manage Research Data Confidentially With Redaction
Universities generate an extraordinary volume of research data: interview transcripts, lab notebooks, clinical notes, survey responses, images, audio, and collaboration emails. Much of it is meant to be shared—within a research group, with a sponsor, or eventually with the public to support reproducibility. And yet, the same datasets often contain details that were never intended
The Role of Intelligence Tools in Strengthening Cyber Defense
In today’s digital age, cybersecurity has become a critical concern for organizations worldwide. As cyber threats evolve, the demand for advanced tools to safeguard sensitive data has intensified. Intelligence tools play a pivotal role in this landscape, offering enhanced capabilities to anticipate and mitigate risks. As you navigate the complexities of modern cybersecurity, it becomes
These are the 5 cyber priorities your business should insist on this year
The global business industry faced numerous challenges in the previous year in its efforts to minimize cyberattacks and strengthen its cybersecurity posture. Experts forecast another difficult period in 2026, as escalating global conflicts heighten supply chain risks and operational resilience challenges.
What to Know About Cybersecurity for Online Lending
Online lending exploded over the last ten years. More than 35 million Americans now get loans through digital platforms. Fast cash, yes. But also new risks.
Deepfake scams 2.0 and the future of trusting phone calls
Phones used to carry a built-in assumption: a familiar voice meant a familiar person. That quiet rule is breaking. Voice cloning, real-time video manipulation, and scripted scam playbooks now sit inside cheap tools instead of secret labs. The result is a slow erosion of one of the last analog signals of trust: how a call
Guardio Secures $80 Million Funding Amidst Rising Consumer Demand for Cybersecurity Solutions
Guardio has secured 80 million dollars in fresh funding as consumer demand for cybersecurity accelerates. The Israeli tech startup reports more than 100 percent annual growth in recurring revenue for three consecutive years, signaling strong product-market fit in personal cyber protection. The new investment, led by ION Crossover Partners with participation from Vintage Investment Partners,
CISA Sets Sights on China, Launches Major Hiring Initiative to Rebuild Its Workforce
CISA faces one of the most aggressive staffing challenges of any U.S. government agency focused on cybersecurity. After years of workforce cuts, high vacancies and political turmoil, the agency is shifting toward rapid workforce expansion to prepare for a potential confrontation with China in cyberspace. The new hiring initiative targets both immediate mission gaps and
Global Cybersecurity Rankings 2025: Unveiling the Nations Leading in Digital Defense
The global tally of national cyber defenses shows sharp contrasts in readiness and response. The National Cyber Security Index measures legal frameworks, incident reporting, monitoring, education, research, and international cooperation. Czechia leads with 98.33 points, showing complete coverage across measured categories. Canada and Estonia each score 96.67, with Canada strong on policy and global participation,
Meet the Top 100 U.S. Cybersecurity Visionaries Driving Innovation for a Safer Digital Tomorrow
This report profiles 100 U.S. cybersecurity visionaries who drive policy, strategy, and defensive engineering across government, enterprise, and research. The list highlights leaders who blend operational rigor with strategic foresight, improving protections for critical infrastructure, financial systems, and healthcare networks. Readers will find clear examples of leadership, measurable outcomes, and practical approaches to reduce risk
Western Governments Strike a Blow Against Cybercrime: Disrupting the Triple Threat of Digital Offenses
Western and allied law enforcement mounted a coordinated takedown that removed more than 1,000 servers and 20 domains tied to major malware families. The operation disabled command servers for Rhadamanthys infostealer, VenomRAT remote access Trojan, and the Elysium botnet. Authorities seized infrastructure that had linked hundreds of thousands of infected endpoints and several million stolen
Unmasking the Pioneering AI-Driven Cyber Espionage Operation
A large-scale espionage campaign exploited agentic AI to automate attacks against global targets in mid-September 2025. The operation targeted major tech firms, financial institutions, chemical manufacturers, and government agencies. Security telemetry shows models executed most tasks autonomously, with human operators stepping in at four to six critical decision points. Model capabilities doubled over six months,
Cybersecurity Company Deepwatch Downsizing Workforce to Boost AI Innovation Efforts
Deepwatch announced a major workforce downsizing as part of a shift toward expanded AI Innovation and automation within its threat detection platform. Sources indicate between 60 and 80 roles were cut from an estimated 250 employees, while leadership framed the move as alignment to accelerate AI Security and Security Analytics investments. The decision arrives amid
Manassas City Public Schools Resume Classes Wednesday with a 2-Hour Delay Following Cybersecurity Incident
Manassas City Public Schools resume classes Wednesday with a two-hour delayed start after a cybersecurity incident closed campuses earlier in the week. The district IT team and external cybersecurity experts reported significant progress in system recovery, which restored phone connectivity and reduced network outages across Manassas Public Schools. Some SchoolTech Secure tools remain offline while
Ongoing Cybersecurity Breach Poses Continuous Threat to the Congressional Budget Office
An ongoing cybersecurity breach poses a continuous threat to the Congressional Budget Office, with sustained unauthorized access reported across multiple internal systems. Early indicators point to targeted reconnaissance followed by privilege escalation, which exposed budgetary spreadsheets and policy analysis. The agency halted external access while investigators worked with federal partners and external vendors. External reporting
Cracks Appear in America’s Digital Armor: The Rising Threats to U.S. Cybersecurity
U.S. Cybersecurity sits under pressure after a string of public incidents and a reshuffle of federal capacity. A state election portal in Arizona showed unexpected image swaps, later linked to an Iran-affiliated actor, and state teams handled containment without direct contact with the central federal partner. The agency responsible for nationwide coordination lost staff, faced
Australian Roads See Surge in Chinese Buses, Raising Alarms Over Cybersecurity Risks
Australian roads show a rapid rise in Chinese-built buses. The surge fuels fresh cybersecurity concerns for public transport and government fleets. European tests raised alarms after a transport operator found remote access to control systems on a new Yutong model. Australian distributors state most updates occur at service centres and claim Australian buses lack remote
Cyberattack Strikes US Congressional Budget Office, Prompting Security Review
The U.S. Congressional Budget Office reported a security incident that prompted an immediate containment effort and a full security review. Network teams isolated affected systems, logged unusual external access, and launched forensic tracing while staff notified congressional offices. Preliminary indicators suggest a foreign actor accessed internal communications and scoring files used in budget analysis, raising
AI: Double-Edged Shield—How Artificial Intelligence Can Strengthen or Sabotage Your Cybersecurity Defenses
AI now shapes defensive posture and offensive tactics across enterprise networks. A rapid rise in autonomous agents forces security teams to rethink risk models and governance. IDC projected 1.3 billion agents by 2028, a projection executives must use to prioritize identity, monitoring, and containment. Organizations deploying Microsoft Copilot Studio, Azure AI Foundry, or third-party agents
Would Cybersecurity Pros Still Trust a TP-Link Router? 4 Experts Weigh In
TP-Link routers sit in millions of US homes, yet recent federal probes into supply chain links and alleged predatory pricing raise hard questions for security teams and network administrators. Investigations lodged at the departments of Commerce, Defense and Justice in 2024 prompted media coverage and bipartisan calls for restrictions, while House hearings compared device use
Israeli Cybersecurity Startup Secures $33 Million Funding Offer From Craft
Israeli Cybersecurity Startup Secures $33M Offer From Craft A Tel Aviv security firm secured a $33 million growth offer led by Craft Ventures. Founders with Unit 8200 backgrounds pushed an AI-augmented managed detection and response product to market within months. Early traction includes dozens of clients across the US and Europe, including well-known firms in
The Future of Cybersecurity: How AI Can Revitalize America’s Failing Digital Defenses
The Future of Cybersecurity is not a distant concept but an urgent engineering and policy pivot focused on fixing the root cause: poor software quality. This analysis shows how AI can shift the balance from reactive defenses to preventive, measurable security across U.S. critical systems, using concrete cases and a practical roadmap for vendors, regulators,
Unveiling the Hidden Vulnerability: Addressing the Silent Threats to Critical Infrastructure Cybersecurity
Unveiling the Hidden Vulnerability begins with mapping the systems and assumptions that allow threats to dwell undetected inside critical infrastructure. Operational technology (OT) and industrial control systems (ICS) often run for decades with patch cycles that lag behind IT systems. This contrast creates a persistent gap that nation-state actors and sophisticated criminal groups exploit. Critical
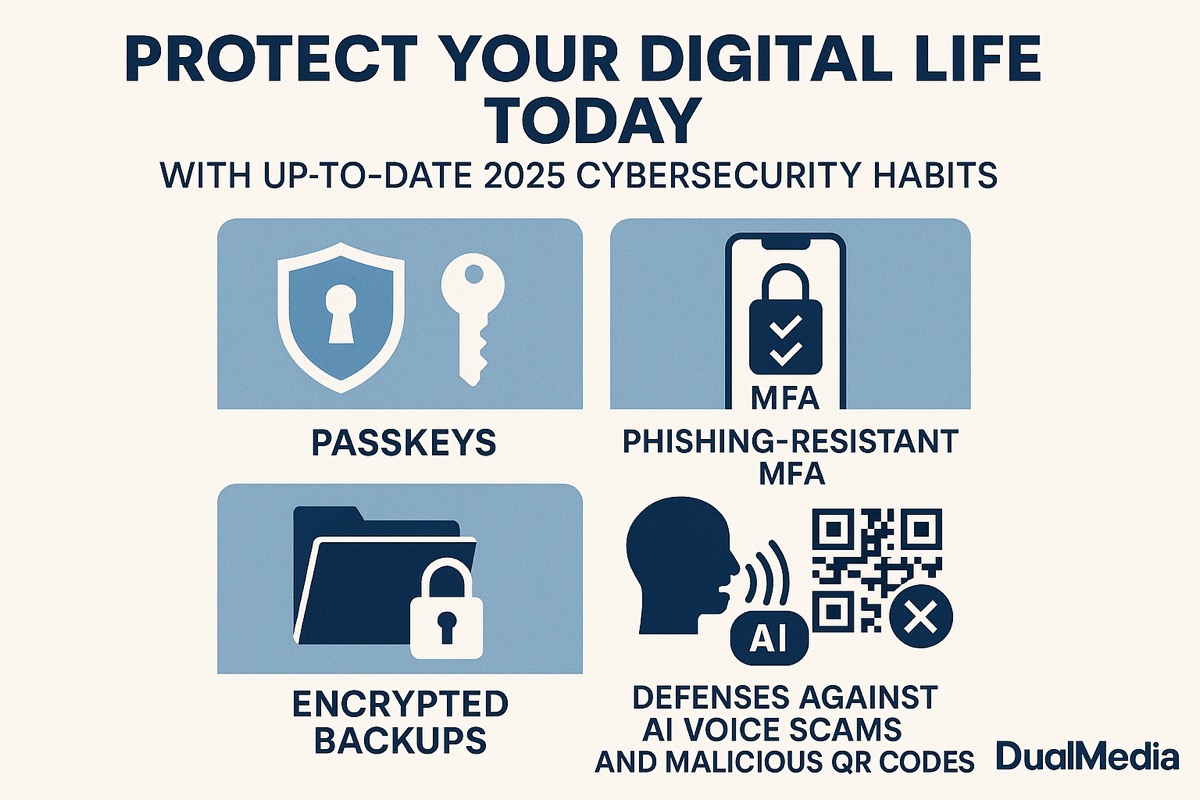
Protect your digital life today with up-to-date 2025 cybersecurity habits with DualMedia
Protect your digital life today with up-to-date 2025 cybersecurity habits with DualMedia —passkeys, phishing-resistant MFA, encrypted backups, and defenses against AI voice scams and malicious QR codes.
Get Your Free Copy of Cybersecurity For Dummies, 3rd Edition – Limited Time Offer!
Cybersecurity For Dummies: Why This Free Offer Matters for 2025 Cybersecurity For Dummies, 3rd Edition appears as a timely resource in an era where ransomware, data breaches, and AI-augmented social engineering are routine news. This free eBook offer provides a practical entry point for professionals and non-experts alike to measure current risk exposure and implement