The global business industry faced numerous challenges in the previous year in its efforts to minimize cyberattacks and strengthen its cybersecurity posture. Experts forecast another difficult period in 2026, as escalating global conflicts heighten supply chain risks and operational resilience challenges.
What to Know About Cybersecurity for Online Lending
Online lending exploded over the last ten years. More than 35 million Americans now get loans through digital platforms. Fast cash, yes. But also new risks.
Deepfake scams 2.0 and the future of trusting phone calls
Phones used to carry a built-in assumption: a familiar voice meant a familiar person. That quiet rule is breaking. Voice cloning, real-time video manipulation, and scripted scam playbooks now sit inside cheap tools instead of secret labs. The result is a slow erosion of one of the last analog signals of trust: how a call
Guardio Secures $80 Million Funding Amidst Rising Consumer Demand for Cybersecurity Solutions
Guardio has secured 80 million dollars in fresh funding as consumer demand for cybersecurity accelerates. The Israeli tech startup reports more than 100 percent annual growth in recurring revenue for three consecutive years, signaling strong product-market fit in personal cyber protection. The new investment, led by ION Crossover Partners with participation from Vintage Investment Partners,
CISA Sets Sights on China, Launches Major Hiring Initiative to Rebuild Its Workforce
CISA faces one of the most aggressive staffing challenges of any U.S. government agency focused on cybersecurity. After years of workforce cuts, high vacancies and political turmoil, the agency is shifting toward rapid workforce expansion to prepare for a potential confrontation with China in cyberspace. The new hiring initiative targets both immediate mission gaps and
Global Cybersecurity Rankings 2025: Unveiling the Nations Leading in Digital Defense
The global tally of national cyber defenses shows sharp contrasts in readiness and response. The National Cyber Security Index measures legal frameworks, incident reporting, monitoring, education, research, and international cooperation. Czechia leads with 98.33 points, showing complete coverage across measured categories. Canada and Estonia each score 96.67, with Canada strong on policy and global participation,
Meet the Top 100 U.S. Cybersecurity Visionaries Driving Innovation for a Safer Digital Tomorrow
This report profiles 100 U.S. cybersecurity visionaries who drive policy, strategy, and defensive engineering across government, enterprise, and research. The list highlights leaders who blend operational rigor with strategic foresight, improving protections for critical infrastructure, financial systems, and healthcare networks. Readers will find clear examples of leadership, measurable outcomes, and practical approaches to reduce risk
Western Governments Strike a Blow Against Cybercrime: Disrupting the Triple Threat of Digital Offenses
Western and allied law enforcement mounted a coordinated takedown that removed more than 1,000 servers and 20 domains tied to major malware families. The operation disabled command servers for Rhadamanthys infostealer, VenomRAT remote access Trojan, and the Elysium botnet. Authorities seized infrastructure that had linked hundreds of thousands of infected endpoints and several million stolen
Unmasking the Pioneering AI-Driven Cyber Espionage Operation
A large-scale espionage campaign exploited agentic AI to automate attacks against global targets in mid-September 2025. The operation targeted major tech firms, financial institutions, chemical manufacturers, and government agencies. Security telemetry shows models executed most tasks autonomously, with human operators stepping in at four to six critical decision points. Model capabilities doubled over six months,
Cybersecurity Company Deepwatch Downsizing Workforce to Boost AI Innovation Efforts
Deepwatch announced a major workforce downsizing as part of a shift toward expanded AI Innovation and automation within its threat detection platform. Sources indicate between 60 and 80 roles were cut from an estimated 250 employees, while leadership framed the move as alignment to accelerate AI Security and Security Analytics investments. The decision arrives amid
Manassas City Public Schools Resume Classes Wednesday with a 2-Hour Delay Following Cybersecurity Incident
Manassas City Public Schools resume classes Wednesday with a two-hour delayed start after a cybersecurity incident closed campuses earlier in the week. The district IT team and external cybersecurity experts reported significant progress in system recovery, which restored phone connectivity and reduced network outages across Manassas Public Schools. Some SchoolTech Secure tools remain offline while
Ongoing Cybersecurity Breach Poses Continuous Threat to the Congressional Budget Office
An ongoing cybersecurity breach poses a continuous threat to the Congressional Budget Office, with sustained unauthorized access reported across multiple internal systems. Early indicators point to targeted reconnaissance followed by privilege escalation, which exposed budgetary spreadsheets and policy analysis. The agency halted external access while investigators worked with federal partners and external vendors. External reporting
Cracks Appear in America’s Digital Armor: The Rising Threats to U.S. Cybersecurity
U.S. Cybersecurity sits under pressure after a string of public incidents and a reshuffle of federal capacity. A state election portal in Arizona showed unexpected image swaps, later linked to an Iran-affiliated actor, and state teams handled containment without direct contact with the central federal partner. The agency responsible for nationwide coordination lost staff, faced
Australian Roads See Surge in Chinese Buses, Raising Alarms Over Cybersecurity Risks
Australian roads show a rapid rise in Chinese-built buses. The surge fuels fresh cybersecurity concerns for public transport and government fleets. European tests raised alarms after a transport operator found remote access to control systems on a new Yutong model. Australian distributors state most updates occur at service centres and claim Australian buses lack remote
Cyberattack Strikes US Congressional Budget Office, Prompting Security Review
The U.S. Congressional Budget Office reported a security incident that prompted an immediate containment effort and a full security review. Network teams isolated affected systems, logged unusual external access, and launched forensic tracing while staff notified congressional offices. Preliminary indicators suggest a foreign actor accessed internal communications and scoring files used in budget analysis, raising
AI: Double-Edged Shield—How Artificial Intelligence Can Strengthen or Sabotage Your Cybersecurity Defenses
AI now shapes defensive posture and offensive tactics across enterprise networks. A rapid rise in autonomous agents forces security teams to rethink risk models and governance. IDC projected 1.3 billion agents by 2028, a projection executives must use to prioritize identity, monitoring, and containment. Organizations deploying Microsoft Copilot Studio, Azure AI Foundry, or third-party agents
Would Cybersecurity Pros Still Trust a TP-Link Router? 4 Experts Weigh In
TP-Link routers sit in millions of US homes, yet recent federal probes into supply chain links and alleged predatory pricing raise hard questions for security teams and network administrators. Investigations lodged at the departments of Commerce, Defense and Justice in 2024 prompted media coverage and bipartisan calls for restrictions, while House hearings compared device use
Israeli Cybersecurity Startup Secures $33 Million Funding Offer From Craft
Israeli Cybersecurity Startup Secures $33M Offer From Craft A Tel Aviv security firm secured a $33 million growth offer led by Craft Ventures. Founders with Unit 8200 backgrounds pushed an AI-augmented managed detection and response product to market within months. Early traction includes dozens of clients across the US and Europe, including well-known firms in
The Future of Cybersecurity: How AI Can Revitalize America’s Failing Digital Defenses
The Future of Cybersecurity is not a distant concept but an urgent engineering and policy pivot focused on fixing the root cause: poor software quality. This analysis shows how AI can shift the balance from reactive defenses to preventive, measurable security across U.S. critical systems, using concrete cases and a practical roadmap for vendors, regulators,
Unveiling the Hidden Vulnerability: Addressing the Silent Threats to Critical Infrastructure Cybersecurity
Unveiling the Hidden Vulnerability begins with mapping the systems and assumptions that allow threats to dwell undetected inside critical infrastructure. Operational technology (OT) and industrial control systems (ICS) often run for decades with patch cycles that lag behind IT systems. This contrast creates a persistent gap that nation-state actors and sophisticated criminal groups exploit. Critical
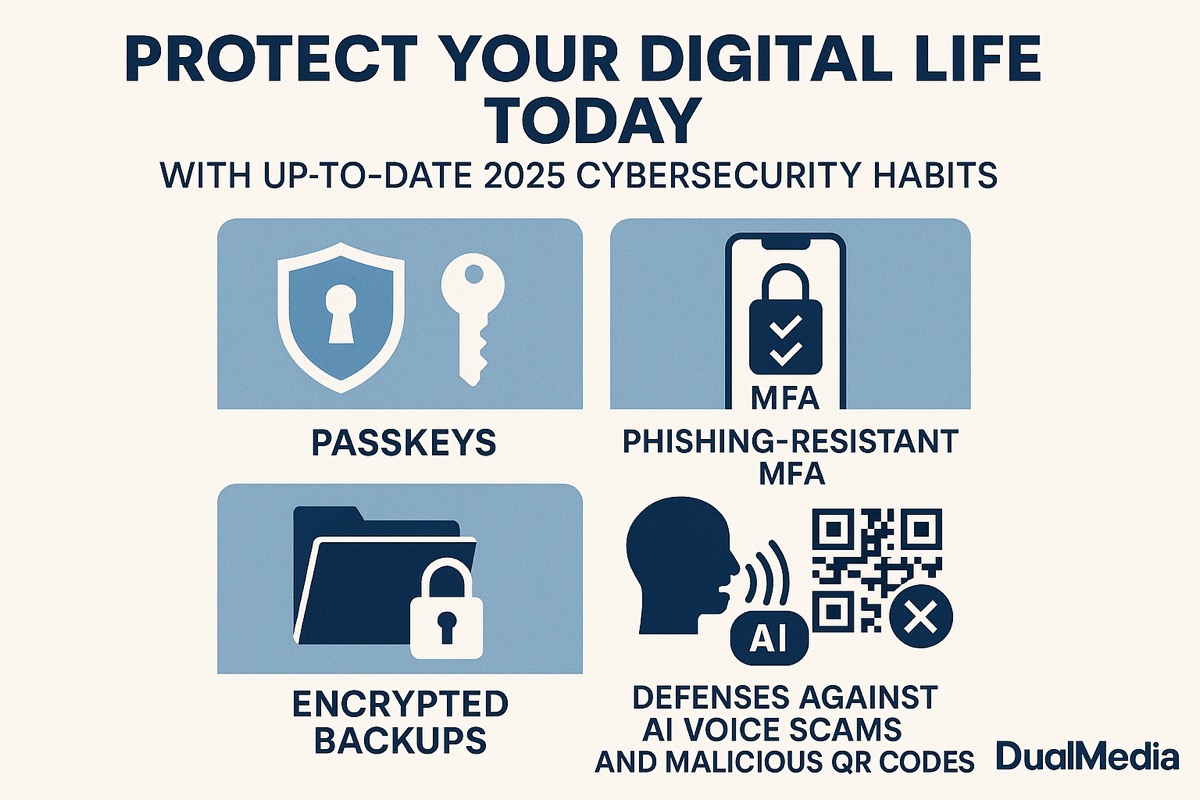
Protect your digital life today with up-to-date 2025 cybersecurity habits with DualMedia
Protect your digital life today with up-to-date 2025 cybersecurity habits with DualMedia —passkeys, phishing-resistant MFA, encrypted backups, and defenses against AI voice scams and malicious QR codes.
Get Your Free Copy of Cybersecurity For Dummies, 3rd Edition – Limited Time Offer!
Cybersecurity For Dummies: Why This Free Offer Matters for 2025 Cybersecurity For Dummies, 3rd Edition appears as a timely resource in an era where ransomware, data breaches, and AI-augmented social engineering are routine news. This free eBook offer provides a practical entry point for professionals and non-experts alike to measure current risk exposure and implement
Cybersecurity Agency in the Crosshairs: Facing Layoffs Amid Government Shutdown After Trump’s Disputes
Cybersecurity Agency in the Crosshairs: Scale and Workforce Impact of Shutdown Layoffs The Cybersecurity Agency landscape shifted abruptly when reductions in force began during the partial federal shutdown. The agency most frequently identified in public reporting experienced large-scale personnel reductions that echo across federal cybersecurity operations. The immediate numerical effects were stark: an agency with
Reallocation of Homeland Security Cyber Experts to Support Trump’s Immigration Enforcement Initiatives
Reallocation of Homeland Security Cyber Experts: Scope and Rationale Behind the Move The Reallocation of Homeland Security Cyber Experts to Support Trump’s Immigration Enforcement Initiatives has become a defining operational shift within the Department of Homeland Security. This reallocation phenomenon involves hundreds of specialists who previously focused on cyber threat alerts, incident response and infrastructure
California’s Leading Cybersecurity Official Advocates for Reform Following Dismissal
California cybersecurity official Dismissal Sparks Calls for Structural Reform The abrupt dismissal of California’s leading cybersecurity official has ignited a technical debate over organizational design, resource allocation, and strategic priorities for state cyber defense. Multiple stakeholders, from state lawmakers to front-line engineers, are evaluating whether the Cybersecurity Integration Center’s placement under the Office of Emergency
How Poker Platforms Keep Online Players Safe From Cyber Threats
Online poker platforms handle millions of transactions daily, with players depositing funds, playing hands, and withdrawing winnings around the clock. Each transaction creates a potential entry point for cybercriminals who want to steal money, personal information, or both. The security measures that poker sites implement determine if players can trust them with their funds and
Filigran, the Cybersecurity Innovator, Secures $58 Million to Propel Global Growth
Filigran Secures $58M: Strategic Funding to Scale Open Threat Management Filigran announced a $58 million Series C funding round that accelerates its mission to advance open threat management across enterprise environments. The capital injection enables rapid scaling of engineering teams, enhancement of AI capabilities, and expansion into new geographies where demand for extended detection and
How Artificial Intelligence is Shaping the Future of Cybersecurity Today
Artificial Intelligence is reshaping digital defenses at a pace that outstrips previous security paradigms. The convergence of machine learning, large language models, and automation is forcing organizations to rethink detection, investigation, and response. This article examines concrete techniques, vendor trends, and operational changes that show how Artificial Intelligence is Shaping the Future of Cybersecurity Today.
Department of Defense to Scale Down Required Cybersecurity Training Programs
The Department of Defense to Scale Down Required Cybersecurity Training Programs has triggered immediate policy changes across the Pentagon, shifting mandatory training frequency, consolidating topics, and authorizing role-based flexibility. This move, ordered in a September memo from senior leadership, aims to reduce time spent on non-warfighting tasks while automating some information management responsibilities. Implementation will
US Department of War Scales Back Cybersecurity Training, Urges Soldiers to Prioritize Core Missions
The US Department of War Scales Back Cybersecurity Training memo has refocused mandatory education toward mission-critical tasks, triggering immediate debate across defense circles. The directive reduces overall training frequency, seeks automation of information management, and narrows Controlled Unclassified Information refreshers, all while emphasizing that personnel must prioritize core warfighting duties. Raised amid a surge in
Expiration of the Cybersecurity Information Sharing Act: Key Updates and Insights from the Cybersecurity Realm
The Cybersecurity Information Sharing Act has entered a phase of legal transition, producing immediate operational friction across private sector incident response, federal threat intelligence programs, and vendor offerings. This report examines the legal, technical, operational and market-level consequences triggered by the lapse of the Cybersecurity Information Sharing Act, using a hypothetical mid-size SOC operator, AtlasSec,
Snyk, the Cybersecurity Innovator, Explores Acquisition Offers Amidst Delays in IPO Aspirations
Snyk, the developer-first cybersecurity firm, has shifted from an imminent IPO trajectory to exploring acquisition proposals as market conditions and execution timelines evolve. The company’s strategic moves — including targeted acquisitions, product integration, and tightening of financial metrics — have drawn interest from strategic buyers and private equity alike. This overview highlights the dynamics of
Impending Expiry of the Cybersecurity Information Sharing Act: What It Means for National Security
The Cybersecurity Information Sharing Act (CISA) faces a built-in expiry at the end of September 2025, and the resulting legal limbo is already reshaping how firms, agencies and incident response teams plan daily operations. This article examines legal, operational, technical and policy dimensions of the impending expiry and places pragmatic scenarios under a realistic light.
Understanding the Rising Challenge of Burnout in the Cybersecurity Field
Rising operational tempo, expanding attack surfaces and a chronic talent gap are accelerating stress across security teams. This article examines how Cybersecurity Burnout manifests, why it intensifies as digital dependency grows, and which structural and individual measures show promise for recovery. Short, evidence-driven analysis and concrete examples anchor each section, with a persistent case thread
Facing Escalating Threats, Cybersecurity Experts Embrace AI Solutions for Enhanced Defense
Facing Escalating Threats, Cybersecurity Experts Embrace AI Solutions for Enhanced Defense has become a defining headline across boardrooms and SOC consoles. Pressure on security teams is rising as attackers leverage automation and generative models to scale social engineering, exploit unpatched vulnerabilities, and craft adaptable malware. In parallel, defenders are accelerating AI adoption to restore signal-to-noise
Preparing for the Future: Key Cyber Security Trends to Watch in 2026
Preparing for the Future: Key Cyber Security Trends to Watch in 2026 sets the stage for an operational roadmap as adversaries exploit agentic AI, deepfakes and nascent quantum capabilities. Threats in 2026 will be shaped by autonomous attack chains, more convincing synthetic media, and encrypted data at risk from future quantum breakthroughs. Organizations that translate
Evaluation Reveals Opportunities for Enhanced Cybersecurity in Utah’s K-12 and Higher Education Institutions
Evaluation Reveals Opportunities for Enhanced Cybersecurity in Utah’s K-12 and Higher Education Institutions — a state legislative audit exposes gaps in baseline defenses, workforce capacity, and governance across public schools and colleges following high-impact breaches. The report references a December 2024 incident affecting roughly 450,000 current and former students in one district and recommends minimum
The Alarming Flaws of DOGE’s Social Security Database: A Deep Dive into a Hidden Cybersecurity Crisis
The Department of Government Efficiency’s rapid creation of a live cloud copy of U.S. citizens’ Social Security records has sparked urgent scrutiny from oversight bodies and cybersecurity professionals. A recent six-month inquiry by the Homeland Security and Governmental Affairs Committee found systemic lapses that created “serious cybersecurity vulnerabilities, privacy violations, and risk of corruption.” With
Covert Cyber Campaigns: China-Connected Entities Targeting Software Providers with Sophisticated Malware
Highly targeted operations tied to China-linked actors have shifted focus upstream, infiltrating software vendors, managed service providers and legal advisers to reach consequential downstream targets. Google and Mandiant telemetry disclosed ongoing activity that leverages stealthy backdoors and long dwell times, enabling exfiltration of source code, privileged correspondence and strategic intelligence. The incidents combine supply-chain thinking
ShadowV2 Botnet Takes Advantage of Misconfigured AWS Docker Containers for DDoS-for-Hire Operations
ShadowV2 represents a new wave of cloud-native threats that convert misconfigured container instances into rentable attack infrastructure. The campaign targets Amazon Web Services (AWS) Docker endpoints exposed to the public internet, deploying a multi-stage toolkit that combines a Python-based command framework and a Go-based remote access trojan. Observed techniques include HTTP/2 Rapid Reset, automated Cloudflare
Exploring the Consequences: When a Cybersecurity Firm Falls Victim to Phishing Attacks
The breach of a single employee account in a security provider exposes systemic risks that ripple beyond a single compromise. This report-style examination frames the fall of a senior employee to a phishing lure as a learning moment for the entire industry, illustrating how a cybersecurity firm can be probed, constrained, and ultimately defended through
Department of Defense Proposes Accelerating Cybersecurity Recruitment to Just 25 Days
The Department of Defense has unveiled a high-velocity plan to compress cybersecurity recruitment timelines to a 25-day target, responding to a persistent deficit of skilled cyber talent that threatens operational readiness. The proposal reframes federal hiring priorities around rapid, skills-based evaluations, AI-enhanced role definitions, and tighter partnerships with industry and academia. Expectations are that accelerating
Rand Paul’s Last-Minute Stipulations Threaten Crucial Cybersecurity Legislation
Rand Paul’s last-minute stipulations have introduced a new level of uncertainty into a Senate effort that had been widely framed as bipartisan and essential. As negotiators in the US Senate scramble, cybersecurity stakeholders are tracking changes that could alter information sharing, liability protections, and the authority of federal agencies charged with protecting critical infrastructure. The
Exploring the Jaguar Land Rover Cyber Breach: Impacts on Smart Factories, Outsourced Security Risks, and Supply Chain Challenges
The Jaguar Land Rover cyber breach exposed critical fault lines in modern automotive manufacturing: interconnected smart factories, heavy reliance on outsourced IT and cybersecurity, and a sprawling supplier network vulnerable to digital disruption. Evidence that systems used to orchestrate production, parts logistics, and engineering workflows were impaired highlights systemic risks that extend beyond a single
Outdated Wireless Vulnerability: Unpatched Firmware Flaws in Routers and Range Extenders
An independent analysis has revealed a troubling persistence: a decade-old wireless flaw remains embedded in shipping and supported firmware across multiple vendors. The report identifies systemic problems in firmware management, delayed patching, and opaque vendor communication that leave small businesses and home users exposed. This article examines the technical mechanics of the vulnerability, the vendors
NIST Invests Over $3 Million to Enhance Cybersecurity Training Initiatives in 13 States
The National Institute of Standards and Technology (NIST) has allocated more than $3.3 million in cooperative agreements to expand community-focused cybersecurity training across 13 states. These awards, distributed through 17 cooperative agreements of roughly $200,000 each, are designed to create Regional Alliances and Multistakeholder Partnerships to Stimulate (RAMPS) that directly map local employer needs to
MorganFranklin Cyber Recognized Among America’s Fastest-Growing Private Companies in 2025
MorganFranklin Cyber has emerged as a standout in 2025, combining rapid revenue expansion with recognized technical depth and a strong internal culture. The firm’s inclusion on the Inc. 5000 list reflects a strategic trajectory following a January divestment that established the cybersecurity unit as a stand‑alone professional services firm. This piece examines the metrics behind
A Promising Israeli Cybersecurity Startup Surfaces from Stealth Mode, Achieving a Valuation of $400 Million
A stealth-mode Israeli cybersecurity startup recently announced a sizable capital injection and a headline valuation that commands attention from enterprise security teams and investors alike. Backed by leading venture firms and staffed by veterans of elite intelligence units, the company claims an architecture designed to reduce detection latency and operational cost by analysing data where
Three Leading Cybersecurity Stocks Worth Investing in This September
Corporate and institutional demand for enterprise-grade security tools has entered a new phase in 2025: persistent threat actors, the ubiquity of cloud infrastructure, and AI-driven attack frameworks are forcing IT budgets to prioritize defense. This pressure has translated into robust revenue growth for a handful of market leaders that combine scale, platform breadth, and AI
Proton Mail Takes Action: Journalist Accounts Suspended Following Cybersecurity Agency Request
Proton Mail suspended multiple journalist accounts after receiving an alert from an unspecified cybersecurity agency about suspected abuse, sparking a public debate over the balance between automated anti-abuse defenses and the needs of reporters handling sensitive disclosures. The incident involved reporters coordinating responsible disclosure of an advanced persistent threat targeting South Korean government networks. Accounts